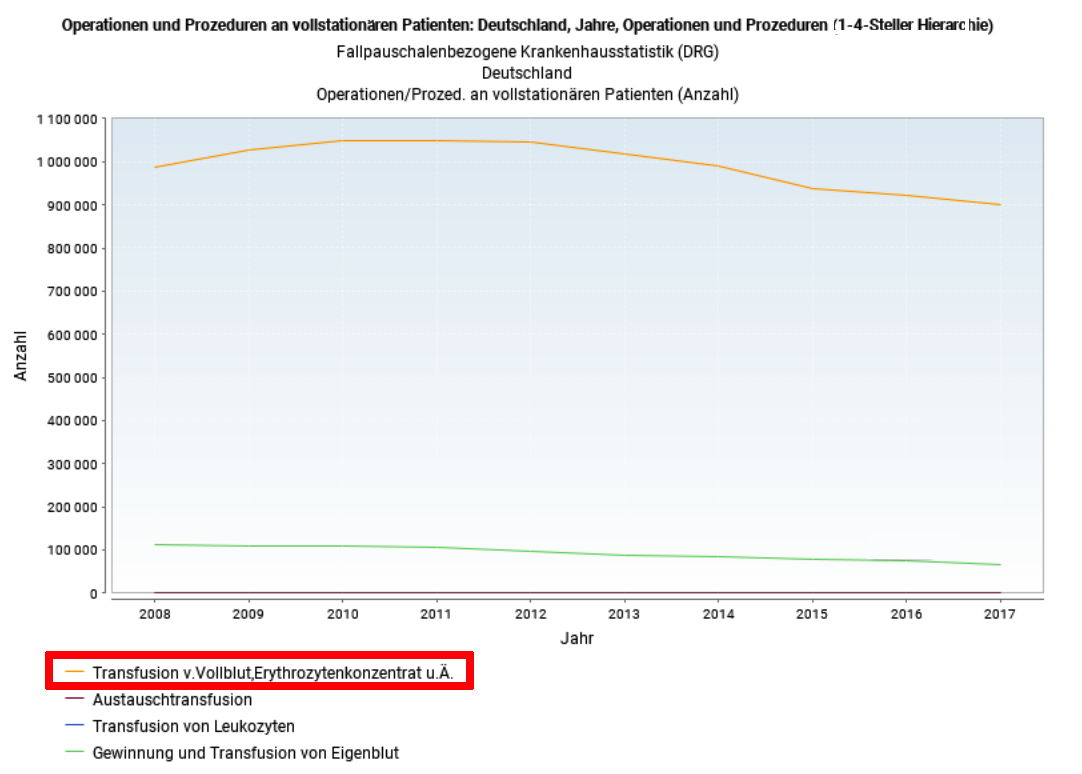
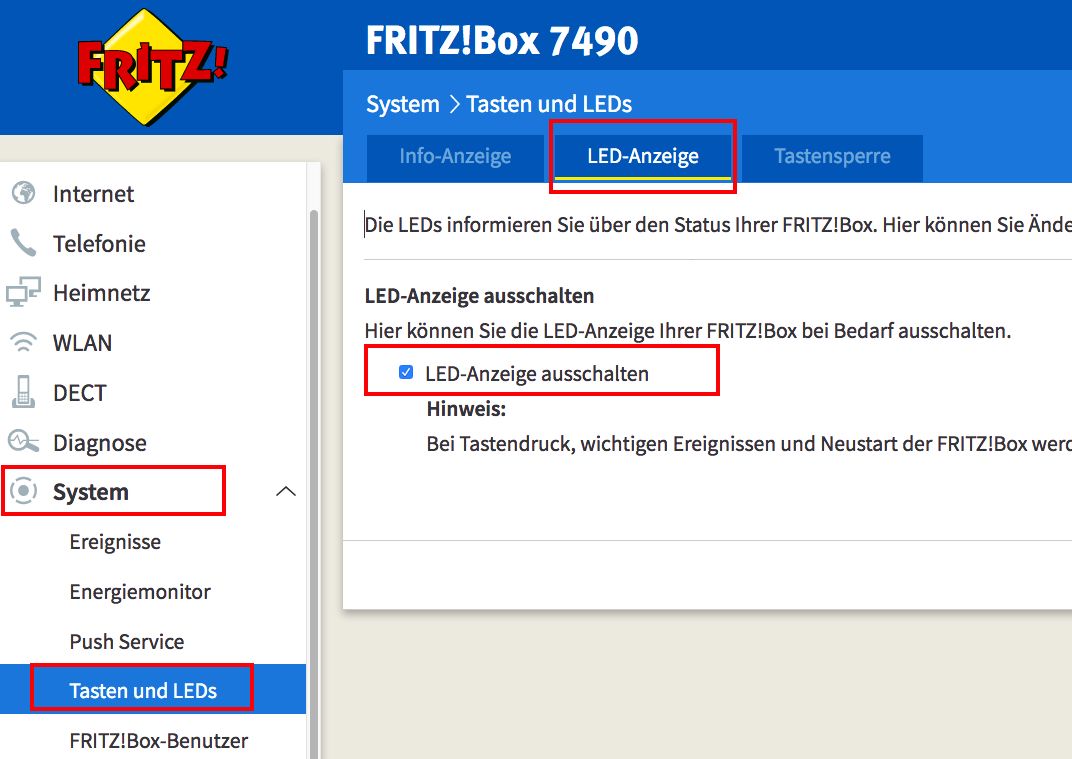
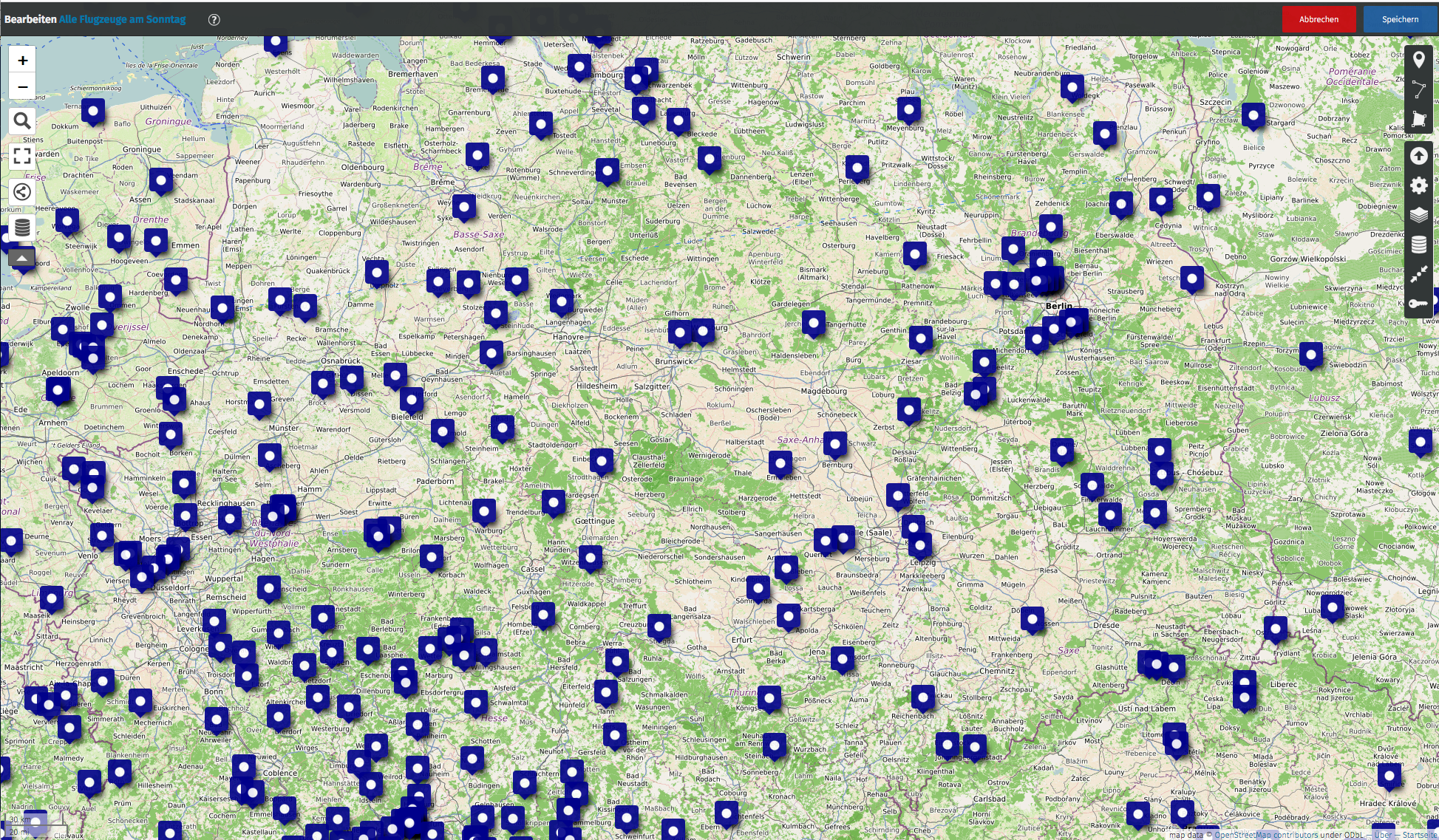
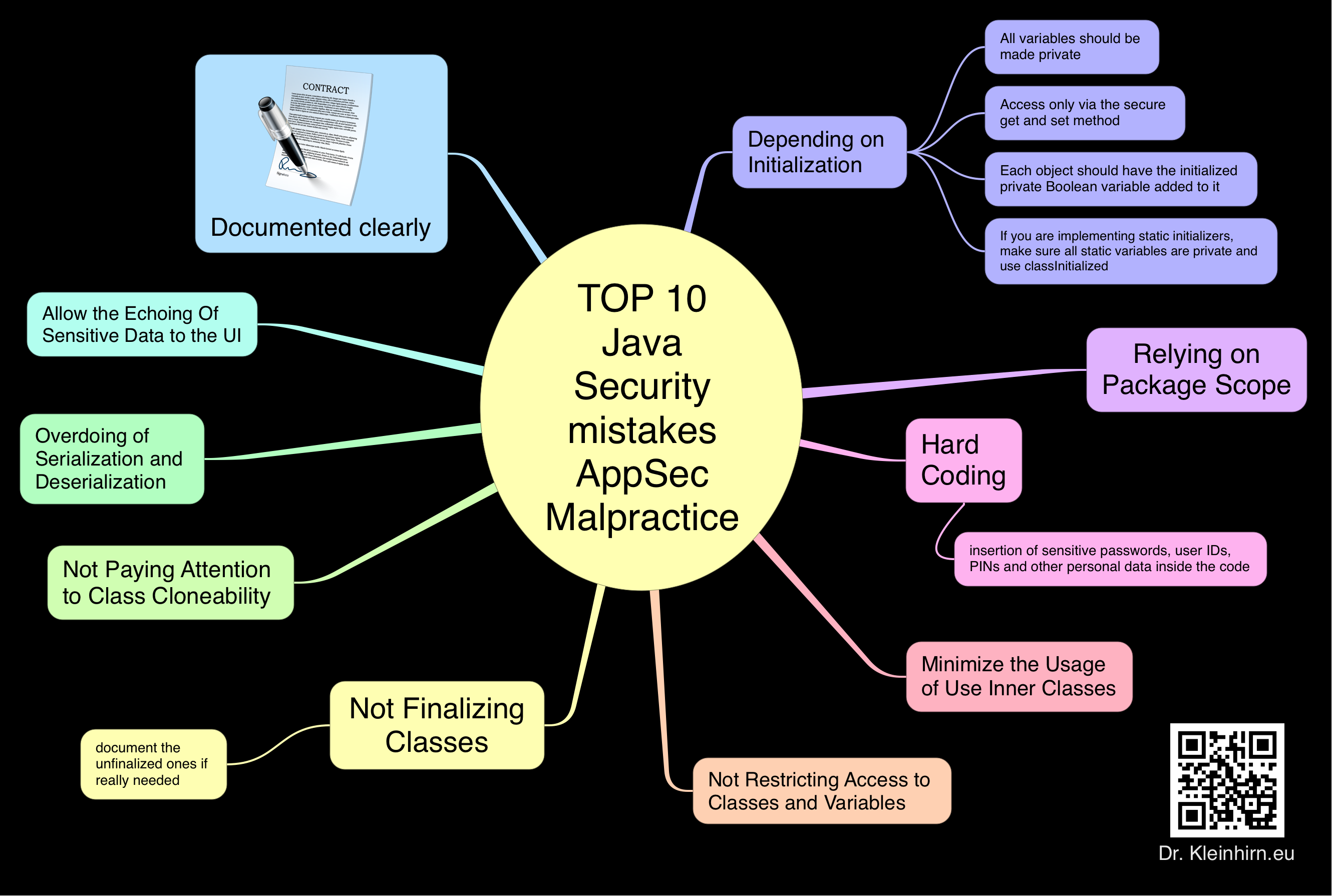
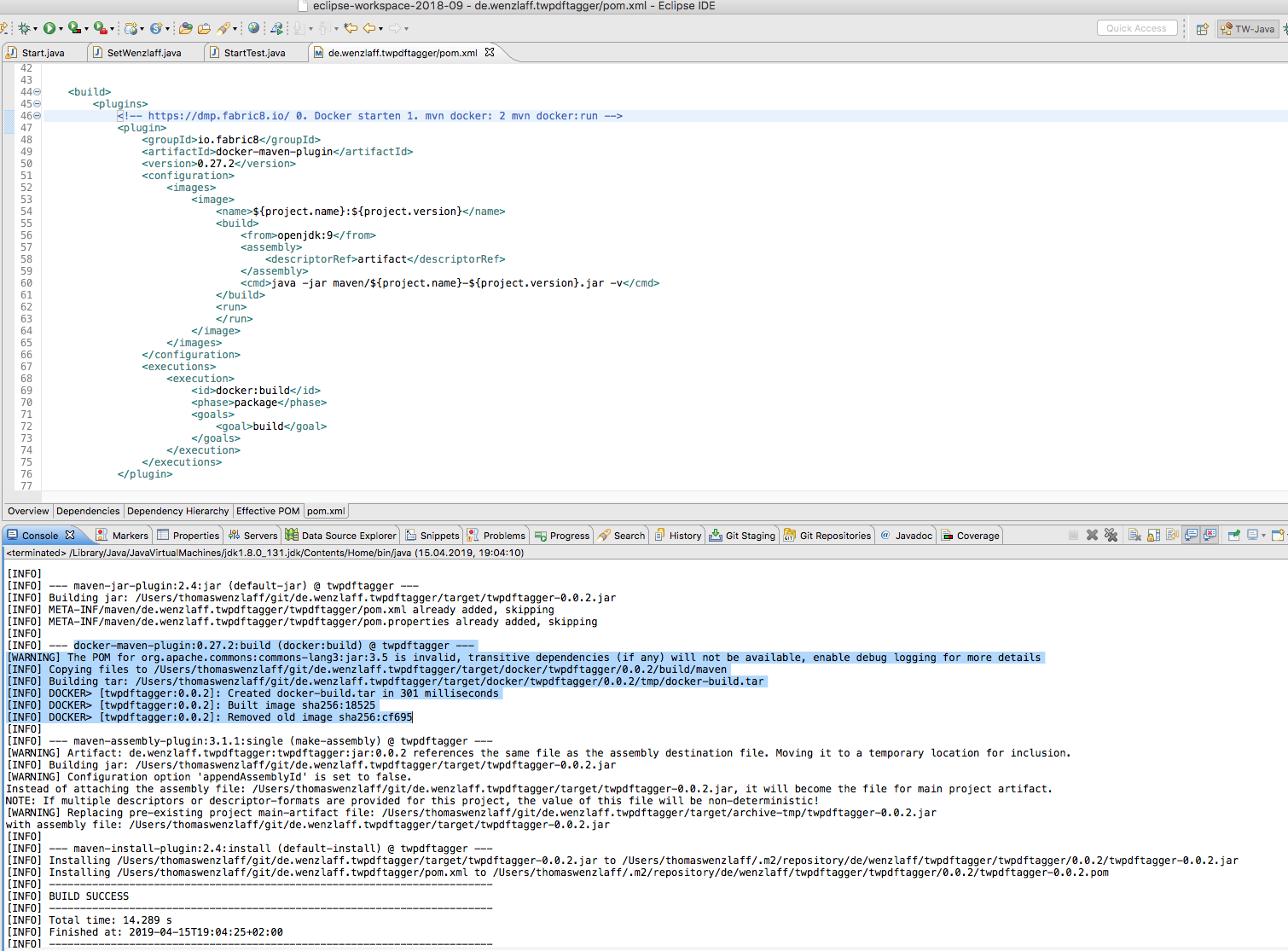
/*
* Wifi Finder der alle fünf Sekunden die Wifis scannt und für jedes freie WLan einmal kurz die LED anschaltet.
*
* Thomas Wenzlaff (c) 2019 www.wenzlaff.info
*/
#include "ESP8266WiFi.h"
void setup() {
Serial.begin(115200);
WiFi.mode(WIFI_STA);
WiFi.disconnect();
delay(100);
pinMode(LED_BUILTIN, OUTPUT);
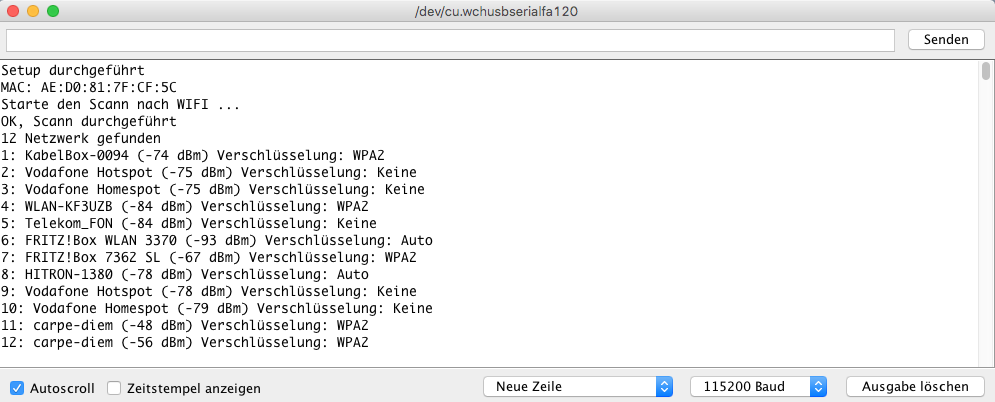
Serial.println("Setup durchgeführt");
printMacAddress();
}
void loop() {
Serial.println("Starte den Scann nach WIFI ...");
digitalWrite(LED_BUILTIN, LOW);
const int n = WiFi.scanNetworks();
Serial.println("OK, Scann durchgeführt");
if (n == 0)
Serial.println("Keine Netzwerke gefunden");
else
{
Serial.print(n);
Serial.println(" Netzwerk gefunden");
for (int i = 0; i < n; ++i)
{
Serial.print(i + 1);
Serial.print(": ");
Serial.print(WiFi.SSID(i));
Serial.print(" (");
Serial.print(WiFi.RSSI(i));
Serial.print(" dBm)");
Serial.print(" Verschlüsselung: ");
printEncryptionType(WiFi.encryptionType(i));
delay(10);
}
}
Serial.println("");
digitalWrite(LED_BUILTIN, HIGH);
delay(5000);
}
void printEncryptionType(int thisType) {
switch (thisType) {
case ENC_TYPE_WEP:
Serial.println("WEP");
break;
case ENC_TYPE_TKIP:
Serial.println("WPA");
break;
case ENC_TYPE_CCMP:
Serial.println("WPA2");
break;
case ENC_TYPE_NONE:
Serial.println("Keine");
digitalWrite(LED_BUILTIN, HIGH);
delay(500);
digitalWrite(LED_BUILTIN, LOW);
break;
case ENC_TYPE_AUTO:
Serial.println("Auto");
break;
}
}
void printMacAddress() {
byte mac[6];
WiFi.macAddress(mac);
Serial.print("MAC: ");
Serial.print(mac[5], HEX);
Serial.print(":");
Serial.print(mac[4], HEX);
Serial.print(":");
Serial.print(mac[3], HEX);
Serial.print(":");
Serial.print(mac[2], HEX);
Serial.print(":");
Serial.print(mac[1], HEX);
Serial.print(":");
Serial.println(mac[0], HEX);
}