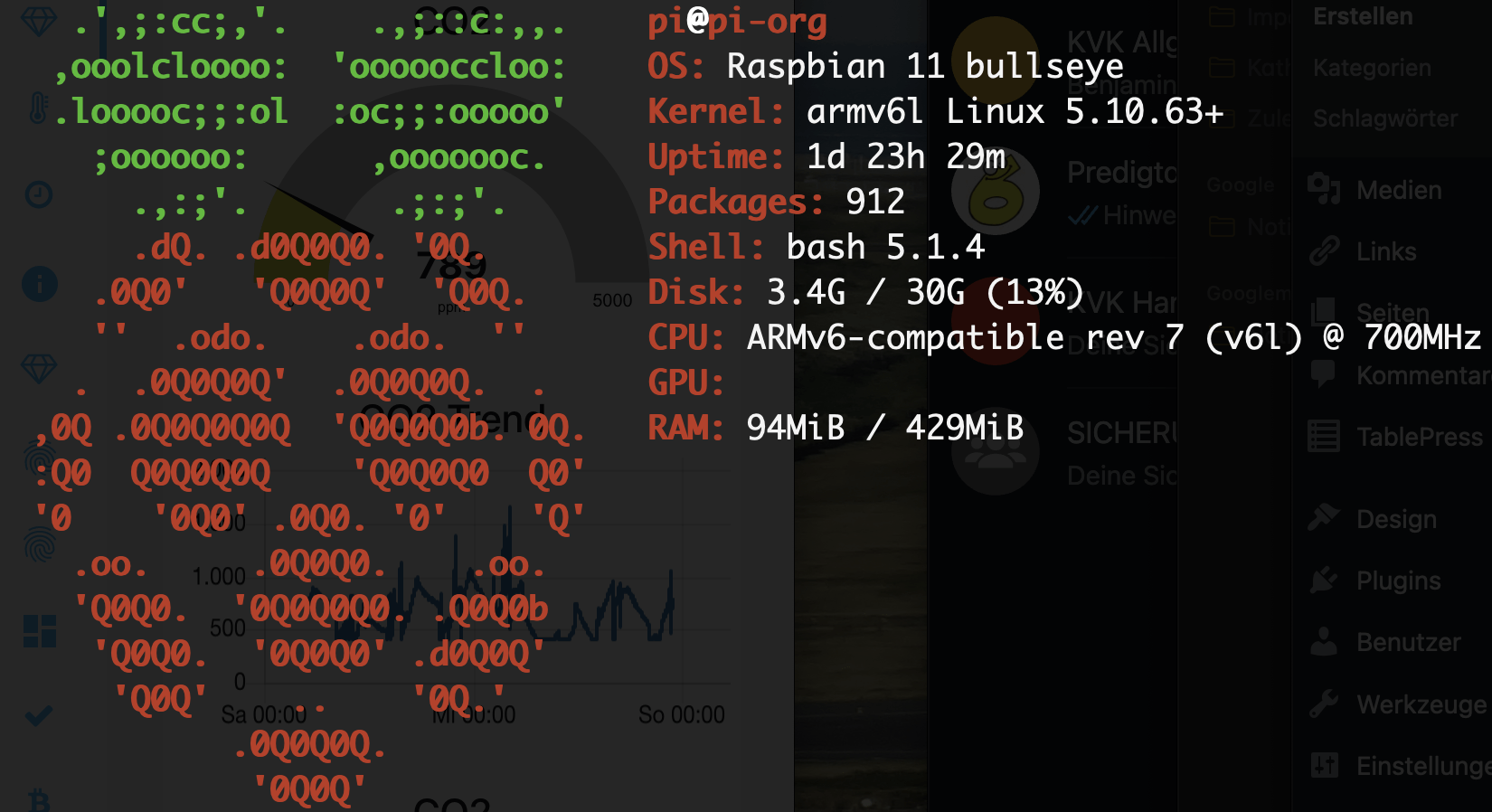
Hatte noch einen Raspberry Pi rumliegen, der Headless mit Raspian 11 bullseye bespielt wurde. Hier ein screenfetch:
Auf den wollen wir nun packet analyzer oder packet sniffer installieren (man braucht dazu kein Kali 😉 ). Hatte in der Vergangenheit schön öfters davon berichtet (1, 2, 3). Tshark ist das Kommandozeilen API für Wireshark.
Installation tshark tcpdump nmap
|
1 2 3 4 5 |
# System updaten sudo apt update sudo apt upgrade # bei der installation von tshark kommt ein Abfrage Dialog, dort mit JA antworten. sudo apt install tshark tcpdump nmap |
Test der Installation und Anleitung
Ausgabe der Anleitung mit tshark -h
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 |
TShark (Wireshark) 3.4.4 (Git v3.4.4 packaged as 3.4.4-1) Dump and analyze network traffic. See https://www.wireshark.org for more information. Usage: tshark [options] ... Capture interface: -i <interface>, --interface <interface> name or idx of interface (def: first non-loopback) -f <capture filter> packet filter in libpcap filter syntax -s <snaplen>, --snapshot-length <snaplen> packet snapshot length (def: appropriate maximum) -p, --no-promiscuous-mode don't capture in promiscuous mode -I, --monitor-mode capture in monitor mode, if available -B <buffer size>, --buffer-size <buffer size> size of kernel buffer (def: 2MB) -y <link type>, --linktype <link type> link layer type (def: first appropriate) --time-stamp-type <type> timestamp method for interface -D, --list-interfaces print list of interfaces and exit -L, --list-data-link-types print list of link-layer types of iface and exit --list-time-stamp-types print list of timestamp types for iface and exit Capture stop conditions: -c <packet count> stop after n packets (def: infinite) -a <autostop cond.> ..., --autostop <autostop cond.> ... duration:NUM - stop after NUM seconds filesize:NUM - stop this file after NUM KB files:NUM - stop after NUM files packets:NUM - stop after NUM packets Capture output: -b <ringbuffer opt.> ..., --ring-buffer <ringbuffer opt.> duration:NUM - switch to next file after NUM secs filesize:NUM - switch to next file after NUM KB files:NUM - ringbuffer: replace after NUM files packets:NUM - switch to next file after NUM packets interval:NUM - switch to next file when the time is an exact multiple of NUM secs Input file: -r <infile>, --read-file <infile> set the filename to read from (or '-' for stdin) Processing: -2 perform a two-pass analysis -M <packet count> perform session auto reset -R <read filter>, --read-filter <read filter> packet Read filter in Wireshark display filter syntax (requires -2) -Y <display filter>, --display-filter <display filter> packet displaY filter in Wireshark display filter syntax -n disable all name resolutions (def: all enabled) -N <name resolve flags> enable specific name resolution(s): "mnNtdv" -d <layer_type>==<selector>,<decode_as_protocol> ... "Decode As", see the man page for details Example: tcp.port==8888,http -H <hosts file> read a list of entries from a hosts file, which will then be written to a capture file. (Implies -W n) --enable-protocol <proto_name> enable dissection of proto_name --disable-protocol <proto_name> disable dissection of proto_name --enable-heuristic <short_name> enable dissection of heuristic protocol --disable-heuristic <short_name> disable dissection of heuristic protocol Output: -w <outfile|-> write packets to a pcapng-format file named "outfile" (or '-' for stdout) --capture-comment <comment> set the capture file comment, if supported -C <config profile> start with specified configuration profile -F <output file type> set the output file type, default is pcapng an empty "-F" option will list the file types -V add output of packet tree (Packet Details) -O <protocols> Only show packet details of these protocols, comma separated -P, --print print packet summary even when writing to a file -S <separator> the line separator to print between packets -x add output of hex and ASCII dump (Packet Bytes) -T pdml|ps|psml|json|jsonraw|ek|tabs|text|fields|? format of text output (def: text) -j <protocolfilter> protocols layers filter if -T ek|pdml|json selected (e.g. "ip ip.flags text", filter does not expand child nodes, unless child is specified also in the filter) -J <protocolfilter> top level protocol filter if -T ek|pdml|json selected (e.g. "http tcp", filter which expands all child nodes) -e <field> field to print if -Tfields selected (e.g. tcp.port, _ws.col.Info) this option can be repeated to print multiple fields -E<fieldsoption>=<value> set options for output when -Tfields selected: bom=y|n print a UTF-8 BOM header=y|n switch headers on and off separator=/t|/s|<char> select tab, space, printable character as separator occurrence=f|l|a print first, last or all occurrences of each field aggregator=,|/s|<char> select comma, space, printable character as aggregator quote=d|s|n select double, single, no quotes for values -t a|ad|adoy|d|dd|e|r|u|ud|udoy output format of time stamps (def: r: rel. to first) -u s|hms output format of seconds (def: s: seconds) -l flush standard output after each packet -q be more quiet on stdout (e.g. when using statistics) -Q only log true errors to stderr (quieter than -q) -g enable group read access on the output file(s) -W n Save extra information in the file, if supported. n = write network address resolution information -X <key>:<value> eXtension options, see the man page for details -U tap_name PDUs export mode, see the man page for details -z <statistics> various statistics, see the man page for details --export-objects <protocol>,<destdir> save exported objects for a protocol to a directory named "destdir" --color color output text similarly to the Wireshark GUI, requires a terminal with 24-bit color support Also supplies color attributes to pdml and psml formats (Note that attributes are nonstandard) --no-duplicate-keys If -T json is specified, merge duplicate keys in an object into a single key with as value a json array containing all values --elastic-mapping-filter <protocols> If -G elastic-mapping is specified, put only the specified protocols within the mapping file Miscellaneous: -h, --help display this help and exit -v, --version display version info and exit -o <name>:<value> ... override preference setting -K <keytab> keytab file to use for kerberos decryption -G [report] dump one of several available reports and exit default report="fields" use "-G help" for more help Dumpcap can benefit from an enabled BPF JIT compiler if available. You might want to enable it by executing: "echo 1 > /proc/sys/net/core/bpf_jit_enable" Note that this can make your system less secure! |
Ausgabe der Anleitung mit nmap -h
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 |
Nmap 7.80 ( https://nmap.org ) Usage: nmap [Scan Type(s)] [Options] {target specification} TARGET SPECIFICATION: Can pass hostnames, IP addresses, networks, etc. Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254 -iL <inputfilename>: Input from list of hosts/networks -iR <num hosts>: Choose random targets --exclude <host1[,host2][,host3],...>: Exclude hosts/networks --excludefile <exclude_file>: Exclude list from file HOST DISCOVERY: -sL: List Scan - simply list targets to scan -sn: Ping Scan - disable port scan -Pn: Treat all hosts as online -- skip host discovery -PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports -PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes -PO[protocol list]: IP Protocol Ping -n/-R: Never do DNS resolution/Always resolve [default: sometimes] --dns-servers <serv1[,serv2],...>: Specify custom DNS servers --system-dns: Use OS's DNS resolver --traceroute: Trace hop path to each host SCAN TECHNIQUES: -sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans -sU: UDP Scan -sN/sF/sX: TCP Null, FIN, and Xmas scans --scanflags <flags>: Customize TCP scan flags -sI <zombie host[:probeport]>: Idle scan -sY/sZ: SCTP INIT/COOKIE-ECHO scans -sO: IP protocol scan -b <FTP relay host>: FTP bounce scan PORT SPECIFICATION AND SCAN ORDER: -p <port ranges>: Only scan specified ports Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9 --exclude-ports <port ranges>: Exclude the specified ports from scanning -F: Fast mode - Scan fewer ports than the default scan -r: Scan ports consecutively - don't randomize --top-ports <number>: Scan <number> most common ports --port-ratio <ratio>: Scan ports more common than <ratio> SERVICE/VERSION DETECTION: -sV: Probe open ports to determine service/version info --version-intensity <level>: Set from 0 (light) to 9 (try all probes) --version-light: Limit to most likely probes (intensity 2) --version-all: Try every single probe (intensity 9) --version-trace: Show detailed version scan activity (for debugging) SCRIPT SCAN: -sC: equivalent to --script=default --script=<Lua scripts>: <Lua scripts> is a comma separated list of directories, script-files or script-categories --script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts --script-args-file=filename: provide NSE script args in a file --script-trace: Show all data sent and received --script-updatedb: Update the script database. --script-help=<Lua scripts>: Show help about scripts. <Lua scripts> is a comma-separated list of script-files or script-categories. OS DETECTION: -O: Enable OS detection --osscan-limit: Limit OS detection to promising targets --osscan-guess: Guess OS more aggressively TIMING AND PERFORMANCE: Options which take <time> are in seconds, or append 'ms' (milliseconds), 's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m). -T<0-5>: Set timing template (higher is faster) --min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes --min-parallelism/max-parallelism <numprobes>: Probe parallelization --min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies probe round trip time. --max-retries <tries>: Caps number of port scan probe retransmissions. --host-timeout <time>: Give up on target after this long --scan-delay/--max-scan-delay <time>: Adjust delay between probes --min-rate <number>: Send packets no slower than <number> per second --max-rate <number>: Send packets no faster than <number> per second FIREWALL/IDS EVASION AND SPOOFING: -f; --mtu <val>: fragment packets (optionally w/given MTU) -D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys -S <IP_Address>: Spoof source address -e <iface>: Use specified interface -g/--source-port <portnum>: Use given port number --proxies <url1,[url2],...>: Relay connections through HTTP/SOCKS4 proxies --data <hex string>: Append a custom payload to sent packets --data-string <string>: Append a custom ASCII string to sent packets --data-length <num>: Append random data to sent packets --ip-options <options>: Send packets with specified ip options --ttl <val>: Set IP time-to-live field --spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address --badsum: Send packets with a bogus TCP/UDP/SCTP checksum OUTPUT: -oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3, and Grepable format, respectively, to the given filename. -oA <basename>: Output in the three major formats at once -v: Increase verbosity level (use -vv or more for greater effect) -d: Increase debugging level (use -dd or more for greater effect) --reason: Display the reason a port is in a particular state --open: Only show open (or possibly open) ports --packet-trace: Show all packets sent and received --iflist: Print host interfaces and routes (for debugging) --append-output: Append to rather than clobber specified output files --resume <filename>: Resume an aborted scan --stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML --webxml: Reference stylesheet from Nmap.Org for more portable XML --no-stylesheet: Prevent associating of XSL stylesheet w/XML output MISC: -6: Enable IPv6 scanning -A: Enable OS detection, version detection, script scanning, and traceroute --datadir <dirname>: Specify custom Nmap data file location --send-eth/--send-ip: Send using raw ethernet frames or IP packets --privileged: Assume that the user is fully privileged --unprivileged: Assume the user lacks raw socket privileges -V: Print version number -h: Print this help summary page. EXAMPLES: nmap -v -A scanme.nmap.org nmap -v -sn 192.168.0.0/16 10.0.0.0/8 nmap -v -iR 10000 -Pn -p 80 SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES |
Ausgabe der Anleitung mit tcpdump -h
|
1 2 3 4 5 6 7 8 9 10 11 |
tcpdump version 4.99.0 libpcap version 1.10.0 (with TPACKET_V3) OpenSSL 1.1.1k 25 Mar 2021 Usage: tcpdump [-AbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ] [--count] [ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ] [ -i interface ] [ --immediate-mode ] [ -j tstamptype ] [ -M secret ] [ --number ] [ --print ] [ -Q in|out|inout ] [ -r file ] [ -s snaplen ] [ -T type ] [ --version ] [ -V file ] [ -w file ] [ -W filecount ] [ -y datalinktype ] [ --time-stamp-precision precision ] [ --micro ] [ --nano ] [ -z postrotate-command ] [ -Z user ] [ expression ] |
Vorhandenen Interfaces ausgeben
tshark -D
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
1. eth0 2. any 3. lo (Loopback) 4. bluetooth-monitor 5. nflog 6. nfqueue 7. dbus-system 8. dbus-session 9. ciscodump (Cisco remote capture) 10. dpauxmon (DisplayPort AUX channel monitor capture) 11. randpkt (Random packet generator) 12. sdjournal (systemd Journal Export) 13. sshdump (SSH remote capture) 14. udpdump (UDP Listener remote capture) |
In welche Formate kann tshark speichern?
Normalerweise speichert man in pcapng Format. Es sind aber auch diese Formate möglich:
tshark -F
Auf dem PI:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
tshark: The available capture file types for the "-F" flag are: 5views - InfoVista 5View capture btsnoop - Symbian OS btsnoop commview - TamoSoft CommView dct2000 - Catapult DCT2000 trace (.out format) erf - Endace ERF capture eyesdn - EyeSDN USB S0/E1 ISDN trace format k12text - K12 text file lanalyzer - Novell LANalyzer logcat - Android Logcat Binary format logcat-brief - Android Logcat Brief text format logcat-long - Android Logcat Long text format logcat-process - Android Logcat Process text format logcat-tag - Android Logcat Tag text format logcat-thread - Android Logcat Thread text format logcat-threadtime - Android Logcat Threadtime text format logcat-time - Android Logcat Time text format modpcap - Modified tcpdump - pcap netmon1 - Microsoft NetMon 1.x netmon2 - Microsoft NetMon 2.x nettl - HP-UX nettl trace ngsniffer - Sniffer (DOS) ngwsniffer_1_1 - NetXray, Sniffer (Windows) 1.1 ngwsniffer_2_0 - Sniffer (Windows) 2.00x niobserver - Network Instruments Observer nokiapcap - Nokia tcpdump - pcap nsecpcap - Wireshark/tcpdump/... - nanosecond pcap nstrace10 - NetScaler Trace (Version 1.0) nstrace20 - NetScaler Trace (Version 2.0) nstrace30 - NetScaler Trace (Version 3.0) nstrace35 - NetScaler Trace (Version 3.5) pcap - Wireshark/tcpdump/... - pcap pcapng - Wireshark/... - pcapng rf5 - Tektronix K12xx 32-bit .rf5 format rh6_1pcap - RedHat 6.1 tcpdump - pcap snoop - Sun snoop suse6_3pcap - SuSE 6.3 tcpdump - pcap visual - Visual Networks traffic capture |
Erzeugen einer pcapng Dump-Datei
Dann mal 10 Sekunden in die Datei traffic-10-sekunden.pcapng den Netzwerkverkehr von 1 (eth0, wie oben) sichern mit:
tshark -i 1 -a duration:10 -w traffic-10-sekunden.pcapng
Als Ergebnis sehen wir einen Counter und den Hinweis das „eth0“ überwacht wird:
|
1 2 |
Capturing on 'eth0' 109 |
Es wird die pcapng (pcap next generation) (früher pcap) Datei geschrieben. Die Formate werden hier beschrieben. Das Format kann mit
file traffic-10-sekunden.pcapng ausgegeben werden:
traffic-10-sekunden.pcapng: pcapng capture file – version 1.0
Es müssen für Tests nicht unbedingt alle Files selbst erzeugt werden, es gibt hier eine Menge Beispiel PCAP/NG-Files zum Download.
Farbe
Es können die Ausgabe auch eingefärbt werden, dazu den Parameter –color anhängen. Wenn das Terminal (bei mir iTerm2) keine Farbe anzeigt, in der ~/.bashrc Datei ein
export COLORTERM=truecolor
anhängen. Dann geht alles mit Farbe in das Terminal z.B.
|
1 |
tshark --color |
Verzeichnise ausgeben
|
1 |
tshark -G folders |
Z.B.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
pi@pi-org:~ $ tshark -G folders Temp: /tmp Personal configuration: /home/pi/.config/wireshark Global configuration: /usr/share/wireshark System: /etc Program: /usr/bin Personal Plugins: /home/pi/.local/lib/wireshark/plugins/3.4 Global Plugins: /usr/lib/arm-linux-gnueabihf/wireshark/plugins/3.4 Personal Lua Plugins: /home/pi/.local/lib/wireshark/plugins Global Lua Plugins: /usr/lib/arm-linux-gnueabihf/wireshark/plugins Extcap path: /usr/lib/arm-linux-gnueabihf/wireshark/extcap MaxMind database path: /usr/share/GeoIP MaxMind database path: /var/lib/GeoIP MaxMind database path: /usr/share/GeoIP MaxMind database path: /var/lib/GeoIP |
Profile ausgeben
|
1 |
tshark -G folders | grep conf | awk -F':\t*' '{print $2"/profiles"}' | xargs ls |
Ergebnis z.B.
|
1 2 3 4 5 |
/home/pi/.config/wireshark/profiles: tw /usr/share/wireshark/profiles: Bluetooth Classic 'No Reassembly' |
Wenn es ein eigenes Profil z.B. wie bei mir mit Namen tw gibt ist das der Name des Verzeichnis, dh. es gib ein Verzeichnis ~/.config/wireshark/profiles/tw und in diesem liegen die Config-Dateien mit festen Namen wie z.B. die colorfilters, preferences oder hosts.
Das Profil kann wie folgt mit dem -C Parameter und dann der Profilename aufgerufen werden, z.B.:
|
1 |
tshark -C tw --color |
Analyse einer pcapng Datei mit capinfos
Um vorhandene pcapng Dateien auszuwerten, kann capinfos verwendet werden. Damit erhält man einen schnellen Überblick z.B. von wann die Aufzeichnungen sind.
capinfos datei-name.pcapng
Ergebnis z.B.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
File name: datei-name.pcapng File type: Wireshark/... - pcapng File encapsulation: Ethernet File timestamp precision: nanoseconds (9) Packet size limit: file hdr: (not set) Number of packets: 86 File size: 11kB Data size: 8,468 bytes Capture duration: 6.982115287 seconds First packet time: 2021-11-22 09:08:15.247428821 Last packet time: 2021-11-22 09:08:22.229544108 Data byte rate: 1,212 bytes/s Data bit rate: 9,702 bits/s Average packet size: 98.47 bytes Average packet rate: 12 packets/s SHA256: 8b42cd6bd297036cadfc7673ff34d20b512349317e2faa824b4edc6b50f94519 RIPEMD160: 7ce5c28d92560d31098b8eee6dfeb76c8451fa60 SHA1: 9e4e43b55d6ddb0fa2aadb527ae2e5c3e14dd7ce Strict time order: True Capture oper-sys: Linux 5.10.63+ Capture application: Dumpcap (Wireshark) 3.4.4 (Git v3.4.4 packaged as 3.4.4-1) Number of interfaces in file: 1 Interface #0 info: Name = eth0 Encapsulation = Ethernet (1 - ether) Capture length = 262144 Time precision = nanoseconds (9) Time ticks per second = 1000000000 Time resolution = 0x09 Operating system = Linux 5.10.63+ Number of stat entries = 1 Number of packets = 86 |
Hier die ganze Anleitung:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 |
Capinfos (Wireshark) 3.4.4 (Git v3.4.4 packaged as 3.4.4-1) Print various information (infos) about capture files. See https://www.wireshark.org for more information. Usage: capinfos [options] <infile> ... General infos: -t display the capture file type -E display the capture file encapsulation -I display the capture file interface information -F display additional capture file information -H display the SHA256, RMD160, and SHA1 hashes of the file -k display the capture comment Size infos: -c display the number of packets -s display the size of the file (in bytes) -d display the total length of all packets (in bytes) -l display the packet size limit (snapshot length) Time infos: -u display the capture duration (in seconds) -a display the capture start time -e display the capture end time -o display the capture file chronological status (True/False) -S display start and end times as seconds Statistic infos: -y display average data rate (in bytes/sec) -i display average data rate (in bits/sec) -z display average packet size (in bytes) -x display average packet rate (in packets/sec) Metadata infos: -n display number of resolved IPv4 and IPv6 addresses -D display number of decryption secrets Output format: -L generate long report (default) -T generate table report -M display machine-readable values in long reports Table report options: -R generate header record (default) -r do not generate header record -B separate infos with TAB character (default) -m separate infos with comma (,) character -b separate infos with SPACE character -N do not quote infos (default) -q quote infos with single quotes (') -Q quote infos with double quotes (") Miscellaneous: -h display this help and exit -C cancel processing if file open fails (default is to continue) -A generate all infos (default) -K disable displaying the capture comment Options are processed from left to right order with later options superseding or adding to earlier options. If no options are given the default is to display all infos in long report output format. |
Tree
Ausgabe von Statistik aus einer Datei. Ohne -q wird auch die Datei noch ausgebeben.
tshark -r datei-name.pcapng -z ptype,tree -q
z.B.
|
1 2 3 4 5 6 7 8 9 10 |
================================================================================================================================== IPv4 Statistics/IP Protocol Types: Topic / Item Count Average Min Val Max Val Rate (ms) Percent Burst Rate Burst Start ---------------------------------------------------------------------------------------------------------------------------------- IP Protocol Types 495 0.0353 100% 1.3700 11.151 TCP 449 0.0320 90.71% 1.3700 11.151 UDP 38 0.0027 7.68% 0.0600 1.539 NONE 8 0.0006 1.62% 0.0200 1.559 ---------------------------------------------------------------------------------------------------------------------------------- |
Analog mit DNS:
tshark -r datei-name.pcapng -z dns,tree -q
z.B.:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 |
============================================================================================================================================== DNS: Topic / Item Count Average Min Val Max Val Rate (ms) Percent Burst Rate Burst Start ---------------------------------------------------------------------------------------------------------------------------------------------- Total Packets 18 0.0018 100% 0.0600 1.539 rcode 18 0.0018 100.00% 0.0600 1.539 No error 18 0.0018 100.00% 0.0600 1.539 opcodes 18 0.0018 100.00% 0.0600 1.539 Standard query 18 0.0018 100.00% 0.0600 1.539 Query/Response 18 0.0018 100.00% 0.0600 1.539 Response 9 0.0009 50.00% 0.0300 1.552 Query 9 0.0009 50.00% 0.0300 1.539 Query Type 18 0.0018 100.00% 0.0600 1.539 PTR (domain name PoinTeR) 6 0.0006 33.33% 0.0200 1.572 AAAA (IPv6 Address) 6 0.0006 33.33% 0.0200 1.539 A (Host Address) 6 0.0006 33.33% 0.0200 1.539 Class 18 0.0018 100.00% 0.0600 1.539 IN 18 0.0018 100.00% 0.0600 1.539 Payload size 18 46.00 29 71 0.0018 100% 0.0600 1.539 Query Stats 0 0.0000 100% - - Qname Len 9 16.33 11 27 0.0009 0.0300 1.539 Label Stats 0 0.0000 - - 2nd Level 6 0.0006 0.0200 1.539 4th Level or more 3 0.0003 0.0100 1.572 3rd Level 0 0.0000 - - 1st Level 0 0.0000 - - Response Stats 0 0.0000 100% - - no. of questions 18 1.00 1 1 0.0018 0.0600 1.552 no. of authorities 18 0.00 0 0 0.0018 0.0600 1.552 no. of answers 18 1.00 1 1 0.0018 0.0600 1.552 no. of additionals 18 0.00 0 0 0.0018 0.0600 1.552 Service Stats 0 0.0000 100% - - request-response time (secs) 9 0.00 0.001041 0.013449 0.0009 0.0300 1.552 no. of unsolicited responses 0 0.0000 - - no. of retransmissions 0 0.0000 - - ---------------------------------------------------------------------------------------------------------------------------------------------- |
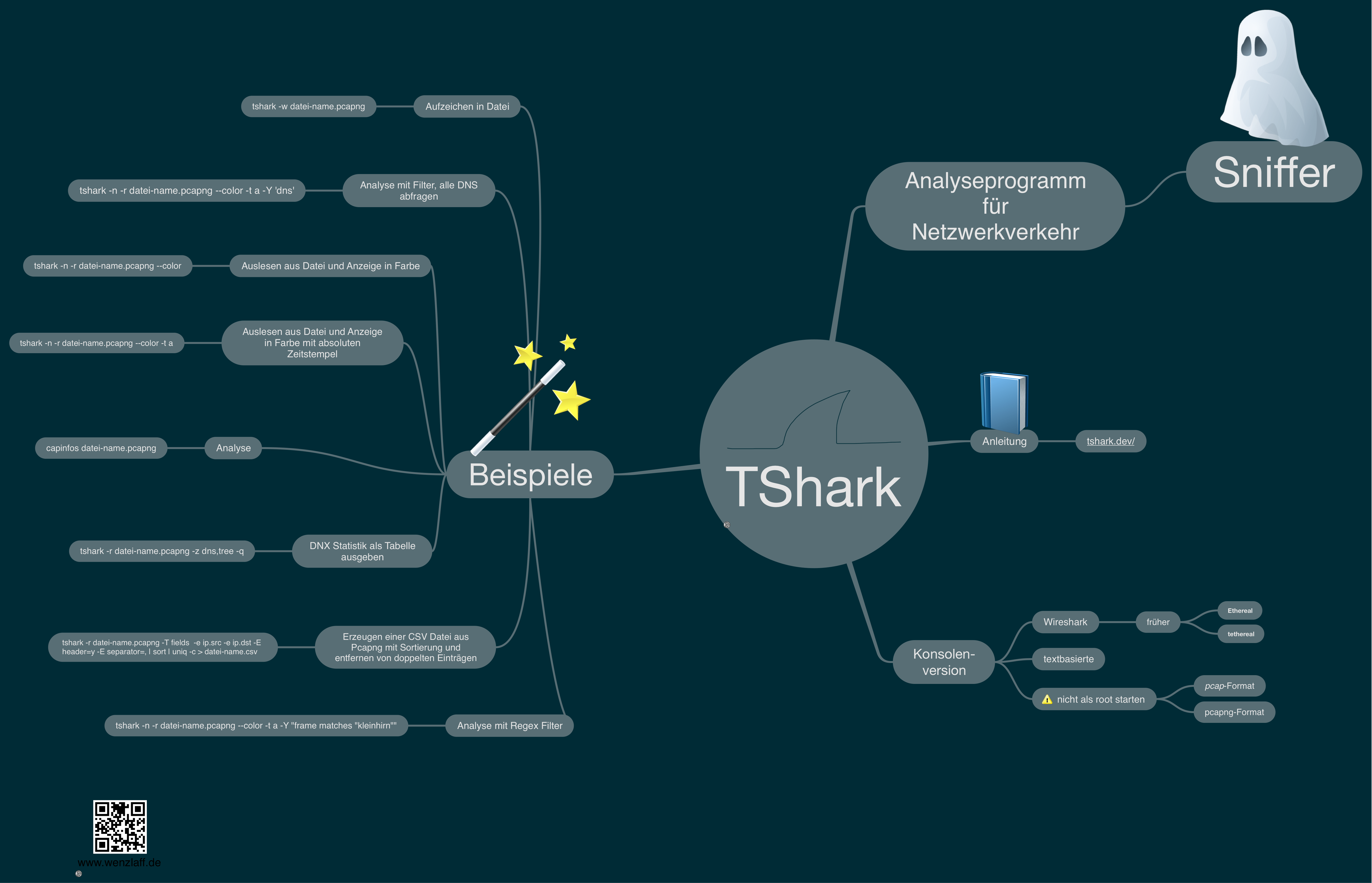
Mindmap