Wer einen eigenen Webserver laufen hat, kann mit nikto einen Sicherheitscann ausführen.
Nikto ist ein in Perl geschriebener Open Source Web Server Scanner. Nikto testet Web Server auf über 7800 potentiell schädliche Dateien und Programme und prüft über 1250 Server-Versionen auf ihre Aktualität und weist bei über 270 Server-Versionen auf bekannte Sicherheitslücken hin. Der Scanner prüft Header und versucht ausserdem, ausnutzbare Fehler und Defaults in der Webserver-Konfiguration aufzudecken. Nikto schickt ca. 7800 GET-Requests an den Webserver, um auf das Vorhandensein unsicherer Inhalte zu prüfen, richtet also keinen Schaden an.
Der ist schnell auf dem Raspberry Pi installiert mit:
sudo apt-get install nikto
Es wir die v2.1.5 installiert. Das kann mit
nikto -Version überprüft werden. Es wird die ausgegeben:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 |
--------------------------------------------------------------------------- Nikto Versions --------------------------------------------------------------------------- File Version Last Mod ----------------------------- -------- ---------- Nikto main 2.1.5 LibWhisker 2.5 CHANGES.txt db_404_strings 2.003 db_content_search 2.000 2012-07-04 1.0 db_embedded 2.004 db_favicon 2.010 db_headers 2.008 db_httpoptions 2.002 db_multiple_index 2.005 db_outdated 2.017 db_parked_strings 2.000 db_realms 2.002 db_server_msgs 2.006 db_subdomains 2.006 db_tests 2.019 db_variables 2.004 nikto_apache_expect_xss.plugin 2.04 nikto_apacheusers.plugin 2.06 nikto_auth.plugin 2.04 nikto_cgi.plugin 2.06 2008-05-06 nikto_clientaccesspolicy.plugin 1.00 nikto_content_search.plugin 2.05 nikto_cookies.plugin 2.03 nikto_core.plugin 2.1.5 nikto_dictionary_attack.plugin 2.04 nikto_embedded.plugin 2.07 nikto_favicon.plugin 2.09 nikto_fileops.plugin 1.00 nikto_headers.plugin 2.10 nikto_httpoptions.plugin 2.10 nikto_msgs.plugin 2.07 nikto_multiple_index.plugin 2.03 nikto_outdated.plugin 2.09 nikto_parked.plugin 2.00 nikto_paths.plugin 2.00 nikto_put_del_test.plugin 2.04 nikto_report_csv.plugin 2.06 2008-11-11 nikto_report_html.plugin 2.05 2009-07-20 nikto_report_msf.plugin 1.00 nikto_report_nbe.plugin 2.01 nikto_report_text.plugin 2.05 2008-11-11 nikto_report_xml.plugin 2.05 2009-07-20 nikto_robots.plugin 2.06 nikto_siebel.plugin 1.00 2011-01-03 nikto_ssl.plugin 2.01 nikto_subdomain.plugin 2.01 nikto_tests.plugin 2.04 2008-09-21 --------------------------------------------------------------------------- Module RPC::XML missing. Logging to Metasploit is disabled. Module RPC::XML::Client missing. Logging to Metasploit is disabled. Undefined subroutine &LW2::init_ssl_engine called at /var/lib/nikto/plugins/nikto_core.plugin line 2499. -config+ Use this config file -Display+ Turn on/off display outputs -dbcheck check database and other key files for syntax errors -Format+ save file (-o) format -Help Extended help information -host+ target host -id+ Host authentication to use, format is id:pass or id:pass:realm -list-plugins List all available plugins -output+ Write output to this file -nossl Disables using SSL -no404 Disables 404 checks -Plugins+ List of plugins to run (default: ALL) -port+ Port to use (default 80) -root+ Prepend root value to all requests, format is /directory -ssl Force ssl mode on port -Tuning+ Scan tuning -timeout+ Timeout for requests (default 10 seconds) -update Update databases and plugins from CIRT.net -Version Print plugin and database versions -vhost+ Virtual host (for Host header) + requires a value Note: This is the short help output. Use -H for full help text. |
Die vollständige Anleitung gibt es mit nikto -Help
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 |
nikto -Help Options: -ask+ Whether to ask about submitting updates yes Ask about each (default) no Don't ask, don't send auto Don't ask, just send -Cgidirs+ Scan these CGI dirs: "none", "all", or values like "/cgi/ /cgi-a/" -config+ Use this config file -Display+ Turn on/off display outputs: 1 Show redirects 2 Show cookies received 3 Show all 200/OK responses 4 Show URLs which require authentication D Debug output E Display all HTTP errors P Print progress to STDOUT S Scrub output of IPs and hostnames V Verbose output -dbcheck Check database and other key files for syntax errors -evasion+ Encoding technique: 1 Random URI encoding (non-UTF8) 2 Directory self-reference (/./) 3 Premature URL ending 4 Prepend long random string 5 Fake parameter 6 TAB as request spacer 7 Change the case of the URL 8 Use Windows directory separator (\) A Use a carriage return (0x0d) as a request spacer B Use binary value 0x0b as a request spacer -Format+ Save file (-o) format: csv Comma-separated-value htm HTML Format msf+ Log to Metasploit nbe Nessus NBE format txt Plain text xml XML Format (if not specified the format will be taken from the file extension passed to -output) -Help Extended help information -host+ Target host -IgnoreCode Ignore Codes--treat as negative responses -id+ Host authentication to use, format is id:pass or id:pass:realm -key+ Client certificate key file -list-plugins List all available plugins, perform no testing -maxtime+ Maximum testing time per host -mutate+ Guess additional file names: 1 Test all files with all root directories 2 Guess for password file names 3 Enumerate user names via Apache (/~user type requests) 4 Enumerate user names via cgiwrap (/cgi-bin/cgiwrap/~user type requests) 5 Attempt to brute force sub-domain names, assume that the host name is the parent domain 6 Attempt to guess directory names from the supplied dictionary file -mutate-options Provide information for mutates -nointeractive Disables interactive features -nolookup Disables DNS lookups -nossl Disables the use of SSL -no404 Disables nikto attempting to guess a 404 page -output+ Write output to this file ('.' for auto-name) -Pause+ Pause between tests (seconds, integer or float) -Plugins+ List of plugins to run (default: ALL) -port+ Port to use (default 80) -RSAcert+ Client certificate file -root+ Prepend root value to all requests, format is /directory -Save Save positive responses to this directory ('.' for auto-name) -ssl Force ssl mode on port -Tuning+ Scan tuning: 1 Interesting File / Seen in logs 2 Misconfiguration / Default File 3 Information Disclosure 4 Injection (XSS/Script/HTML) 5 Remote File Retrieval - Inside Web Root 6 Denial of Service 7 Remote File Retrieval - Server Wide 8 Command Execution / Remote Shell 9 SQL Injection 0 File Upload a Authentication Bypass b Software Identification c Remote Source Inclusion x Reverse Tuning Options (i.e., include all except specified) -timeout+ Timeout for requests (default 10 seconds) -Userdbs Load only user databases, not the standard databases all Disable standard dbs and load only user dbs tests Disable only db_tests and load udb_tests -until Run until the specified time or duration -update Update databases and plugins from CIRT.net -useproxy Use the proxy defined in nikto.conf -Version Print plugin and database versions -vhost+ Virtual host (for Host header) + requires a value |
So nun der 1. Scann gegen den eigenen Webserver und das Ergebnis wird in eine HTML Datei geschrieben.
nikto -h localhost -o nikto-report-server.html
Auf der Konsole wird nun nach ein paar Sekunden das Ergebnis ausgegeben:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
- Nikto v2.1.5 --------------------------------------------------------------------------- + Target IP: 127.0.0.1 + Target Hostname: localhost + Target Port: 80 + Start Time: 2021-06-06 17:35:07 (GMT2) --------------------------------------------------------------------------- + Server: nginx + Server leaks inodes via ETags, header found with file /, fields: 0x60bb5ddc 0x1bc + The anti-clickjacking X-Frame-Options header is not present. + No CGI Directories found (use '-C all' to force check all possible dirs) + 6544 items checked: 0 error(s) and 2 item(s) reported on remote host + End Time: 2021-06-06 17:36:13 (GMT2) (66 seconds) --------------------------------------------------------------------------- + 1 host(s) tested |
Und es wird ein schöner HTML Report im lokalen Verzeichnis erstellt:
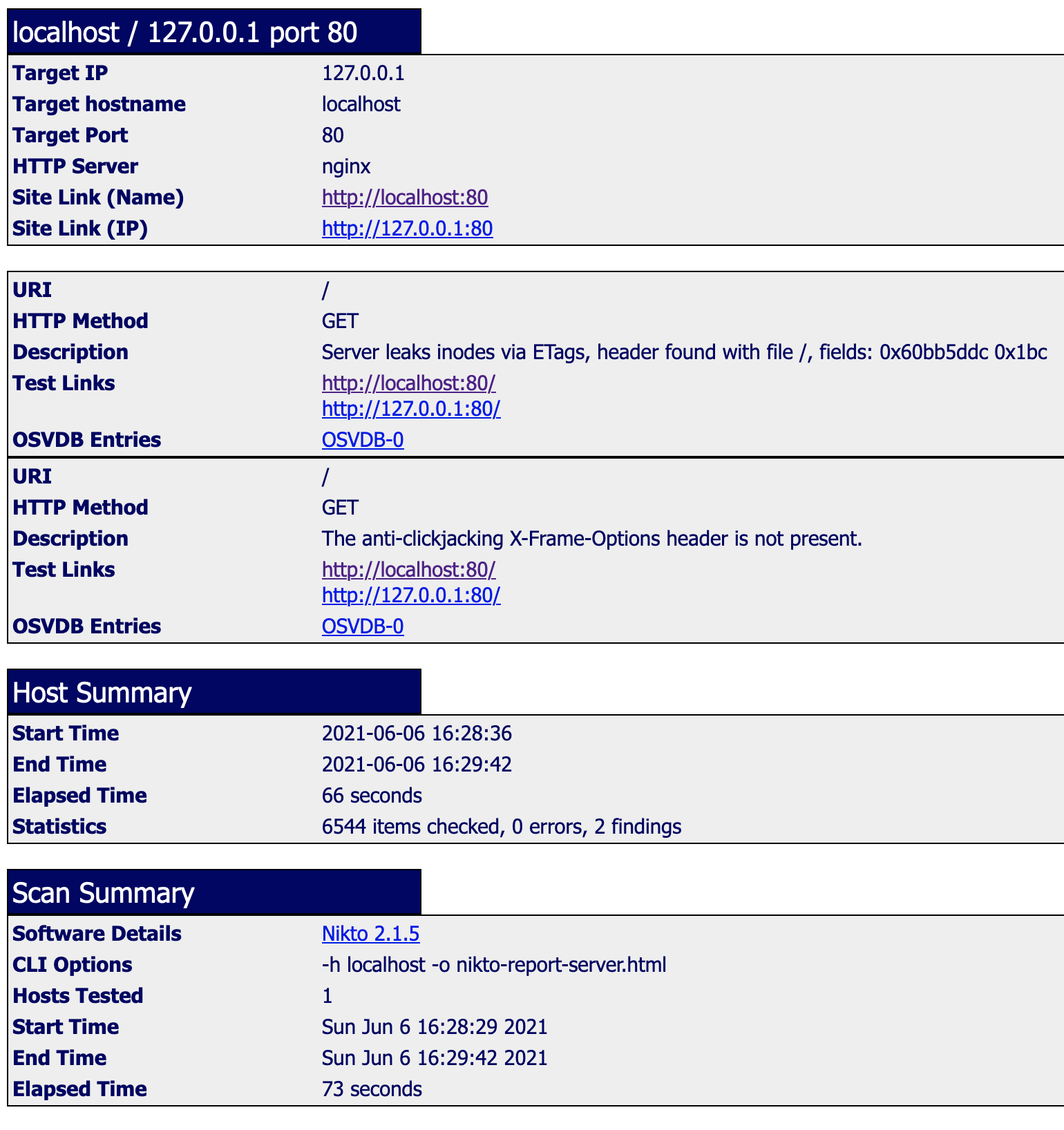
Wer die aktuellste Version v2.1.6 haben will, kann sie clonen und ausführen. Es werden dann einige mehr Request (7855 anstatt 6544) erzeugt. Z.B. wurde dann bei mir auch eine fehlerhafte Seite angemerkt, da kann ich dann mal was tun:
The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type.
Um die neue Version auszuführen:
|
1 2 3 |
git clone https://github.com/IT-Berater/nikto.git cd nikto/program ./nikto.pl -h localhost |
Disclaimer: Bitte beachten, dass es illegal und strafbar ist, Hosts ohne schriftliche Genehmigung zu scannen.
Verwenden Sie nikto nicht auf fremde Server an! Sondern verwenden Sie nur den eigenen Server oder VMs für Übungs- und Testzwecke.
