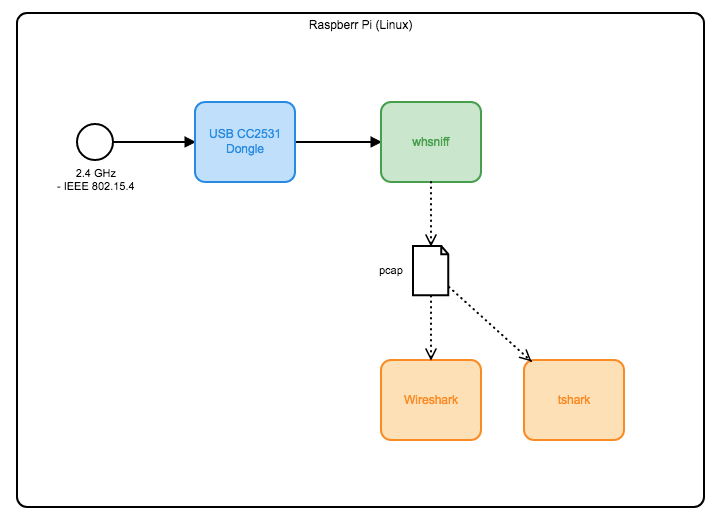
Whsniff ist ein Kommandozeilen Werkzeug für das TI CC2531 USB Dongle für IEEE 802.15.4 Traffic bei 2.4 GHz. Es läuft auf dem Raspberry Pi unter Linux (unter Windows geht wohl auch mit SmartRF von TI).
Und es erzeugt Datein im freien pcap Format (packet capture) für tshark und Wireshark.
Der USB Dongel, Details hatte ich ja schon geschrieben:
Wie können wir das ganze zum laufen bringen?
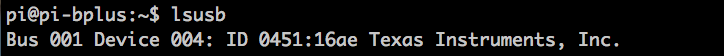
Also erst einmal den USB-Sniffer in den Pi stecken und schauen ob er erkannt wird mit lsusb:
Das sieht ja schon mal ganz gut aus.
Dann compilieren und installieren wir whsniff und tshark. Dafür können wir dieses install-whsniff.sh Script verwenden:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
#!/bin/bash # # Thomas Wenzlafff # cd ~ sudo apt-get update sudo apt-get upgrade sudo apt-get install libusb-1.0-0-dev tshark # wir holen uns das whsniff von GitHub und compilieren es curl -L https://github.com/homewsn/whsniff/archive/v1.1.tar.gz | tar zx cd whsniff-1.1 make sudo make install |
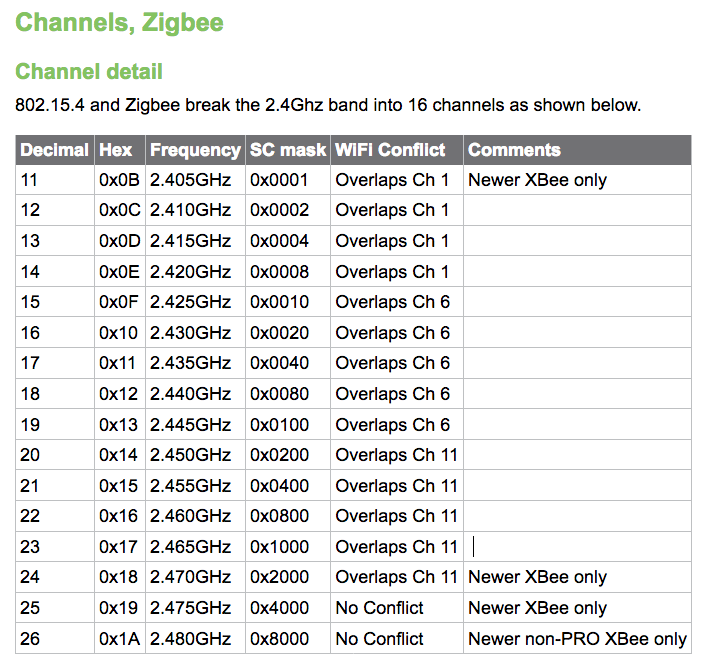
Nun können wir schon anfangen, wir starten mal auf Kanal 18. Hier mal eine Übersicht der 16 möglichen Kanäle (11-26), Zitat:
# Sniff …
whsniff -c 18 > whsniff-log.pcap
Abbruch mit CTRL-C dann haben wir die pcap Datei und können sie auswerten:
# Auswerten der pcap Datei mit tshark
tshark -r whsniff-log.pcap
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# Ergebnis (anonymisiert) z.B.: 0.000000 → IEEE 802.15.4 49 Command 2 249.791641 → 73:8a:15:f7:87:e3:b0:8d IEEE 802.15.4 19 Ack, Dst: 73:8a:22:f7:87:e3:b0:8d[Malformed Packet] 3 1738.283546 0x7912 → IEEE 802.15.4 11 Ack, Src: 0x7912, Bad FCS 4 2979.236975 → IEEE 802.15.4 36 Reserved 5 3016.231398 → IEEE 802.15.4 32 Multipurpose 6 3043.240983 0xb59c → 0x92f7 IEEE 802.15.4 64 Multipurpose, Dst: 0x92f7, Src: 0xb59c, Bad FCS 7 3874.275716 → IEEE 802.15.4 37 Multipurpose 8 4009.222298 → IEEE 802.15.4 31 Extended 9 4628.215064 → IEEE 802.15.4 31 Extended 10 5450.214312 → IEEE 802.15.4 28 Reserved, Bad FCS 11 5960.207120 → 52:13:f0:9b:19:bf:de:9c IEEE 802.15.4 29 Multipurpose, Dst: 52:13:f0:9b:19:bf:de:9c, Bad FCS |
# Oder Auswertung mit …
tshark -r whsniff-log.pcap -V
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 |
# Ergebnis (anonymisiert) z.B.: Frame 1: 49 bytes on wire (392 bits), 49 bytes captured (392 bits) Encapsulation type: IEEE 802.15.4 Wireless PAN (104) Arrival Time: Jan 1, 1970 01:01:02.005144000 CET [Time shift for this packet: 0.000000000 seconds] Epoch Time: 62.005144000 seconds [Time delta from previous captured frame: 0.000000000 seconds] [Time delta from previous displayed frame: 0.000000000 seconds] [Time since reference or first frame: 0.000000000 seconds] Frame Number: 1 Frame Length: 49 bytes (392 bits) Capture Length: 49 bytes (392 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: wpan] IEEE 802.15.4 Command Frame Control Field: 0x3ec3, Frame Type: Command, PAN ID Compression, Information Elements Present, Destination Addressing Mode: Long/64-bit, Frame Version: Reserved, Source Addressing Mode: None .... .... .... .011 = Frame Type: Command (0x3) .... .... .... 0... = Security Enabled: False .... .... ...0 .... = Frame Pending: False .... .... ..0. .... = Acknowledge Request: False .... .... .1.. .... = PAN ID Compression: True .... ...0 .... .... = Sequence Number Suppression: False .... ..1. .... .... = Information Elements Present: True .... 11.. .... .... = Destination Addressing Mode: Long/64-bit (0x3) ..11 .... .... .... = Frame Version: Reserved (3) 00.. .... .... .... = Source Addressing Mode: None (0x0) Sequence Number: 16 [Expert Info (Error/Malformed): Frame Version Unknown Cannot Dissect] [Frame Version Unknown Cannot Dissect] [Severity level: Error] [Group: Malformed] Frame 2: 19 bytes on wire (152 bits), 19 bytes captured (152 bits) Encapsulation type: IEEE 802.15.4 Wireless PAN (104) Arrival Time: Jan 1, 1970 01:05:11.796785000 CET [Time shift for this packet: 0.000000000 seconds] Epoch Time: 311.796785000 seconds [Time delta from previous captured frame: 249.791641000 seconds] [Time delta from previous displayed frame: 249.791641000 seconds] [Time since reference or first frame: 249.791641000 seconds] Frame Number: 2 Frame Length: 19 bytes (152 bits) Capture Length: 19 bytes (152 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: wpan] IEEE 802.15.4 Ack, Sequence Number: 60, Dst: 72:8a:15:f7:87:e3:b2:8d Frame Control Field: 0xceb2, Frame Type: Ack, Frame Pending, Acknowledge Request, Information Elements Present, Destination Addressing Mode: Long/64-bit, Frame Version: IEEE Std 802.15.4-2003, Source Addressing Mode: Long/64-bit .... .... .... .010 = Frame Type: Ack (0x2) .... .... .... 0... = Security Enabled: False .... .... ...1 .... = Frame Pending: True .... .... ..1. .... = Acknowledge Request: True .... .... .0.. .... = PAN ID Compression: False .... ...0 .... .... = Sequence Number Suppression: False .... ..1. .... .... = Information Elements Present: True .... 11.. .... .... = Destination Addressing Mode: Long/64-bit (0x3) ..00 .... .... .... = Frame Version: IEEE Std 802.15.4-2003 (0) 11.. .... .... .... = Source Addressing Mode: Long/64-bit (0x3) Sequence Number: 60 Destination PAN: 0xe30d Destination: 73:8a:15:f7:82:e3:b0:8d (73:8a:15:f2:87:e3:b0:8d) Source PAN: 0x2462 [Malformed Packet: IEEE 802.15.4] [Expert Info (Error/Malformed): Malformed Packet (Exception occurred)] [Malformed Packet (Exception occurred)] [Severity level: Error] [Group: Malformed] ... |